.jpg?ext=.jpg)
Smithers Cybersecurity Webinar Library

If you missed previous webinars, you can view any past presentation on demand by clicking any of the links below.
Insider Threats
Date: Wednesday, November 6, 2024
Time: 1:00 PM EST
In this webinar, Smithers Senior IT Manager Colin Christman walks through the definition of insider threats, how they can be prevented, and how preventing insider-related cybersecurity incidents ties into ISO 27001.

Enter your email address to view this video.
47:05
The Benefits of ISO 27001
Date: Wednesday, October 2, 2024
Time: 2:00 PM EST

Enter your email address to view this video.
44:07
Mobile Devices and Cybersecurity
Date: Wednesday, August 22, 2024
Time: 1:00 PM EST
In this webinar, learn about how devices like smart phones may be impacted by the new CMMC rule. Also learn how to protect your company from insider threats caused by smart device actions.

1:04:31
Enter your email address to view this video.
The Value of Encryption
Date: Wednesday, June 26, 2024
Time: 1:00 PM EST
If you have begun your compliance journey with NIST SP 800-171r2 or ISO 27001, you probably have seen the word “encryption” quite often. In this webinar cybersecurity expert Robert McVay defines encryption, describes what should be encrypted and what should not be, plus much more.

54:14
Enter your email address to view this video.
Setting Scope for Your NIST Assessment
Date: Thursday, May 23, 2024
Time: 1:00 PM EST
One of the most important keys to a successful NIST/CMMC assessment is to establish your scope. Everything truly progresses based on how much is in the scope. In this webinar, Robert McVay walks through the ins and outs of creating a realistic and effective scope for assessment.

Enter your email address to view this video.
32:00
Ransomware Preparedness: Safeguarding Your Organization Against Digital Extortion
Date: Wednesday, April 24, 2024
Time: 1:00 PM EST
You have likely heard of ransomware, but do you know how to define it? In this webinar, learn what ransomware is, how it spreads, and how you can defense your company's defenses.
Enter your email address to view this video.
41:51
Specialized Assets
Date: Wednesday, March 20, 2024
Time: 1:00 PM EST
What is a specialized asset? They are mentioned fairly often in the published CMMC proposed rule. Do you have a specialized asset? Do you have to include it or them in your assessment scope?

Enter your email address to view this video.
24:40
Maintaining CUI in an ERP
Date: Wednesday, January 24, 2024
Time: 1 PM - 2 PM EST
Many businesses that are going to have to comply with NIST/CMMC have ERPs in use. What should you be aware of if your ERP stores CUI? Robert McVay walks through several important pointers in this informative webinar.

Enter your email address to view this video.
44:49
Ten Common Challenges to NIST SP 800-171 Compliance
Date: Wednesday, December 6
Time: 1 PM - 2 PM EST
Many different types of companies are in the process of pursuing compliance with NIST SP 800-171. Despite the variety in the companies, the same controls tend to become obstacles in the process. In this webinar, Robert McVay will review ten of the most common controls that prevent companies from achieving compliance. There is a lot that can be learned from analyzing these specific controls and what they require.
Enter your email address to view this video.
48:08
Can Moving to the Cloud Help Diminish the Risk of a Cyber Breach?
October 18, 2023
In this webinar, Smithers Senior IT Manager Colin Christman walks through the definition of cloud computing, how to share responsibility with a cloud services provider as well as other types of providers, and the pros and cons of moving to a cloud environment. If you are wondering if moving your data to the cloud will increase the security of your IT ecosystem, this webinar will help you move forward.

Enter your email address to view this video.
36:08
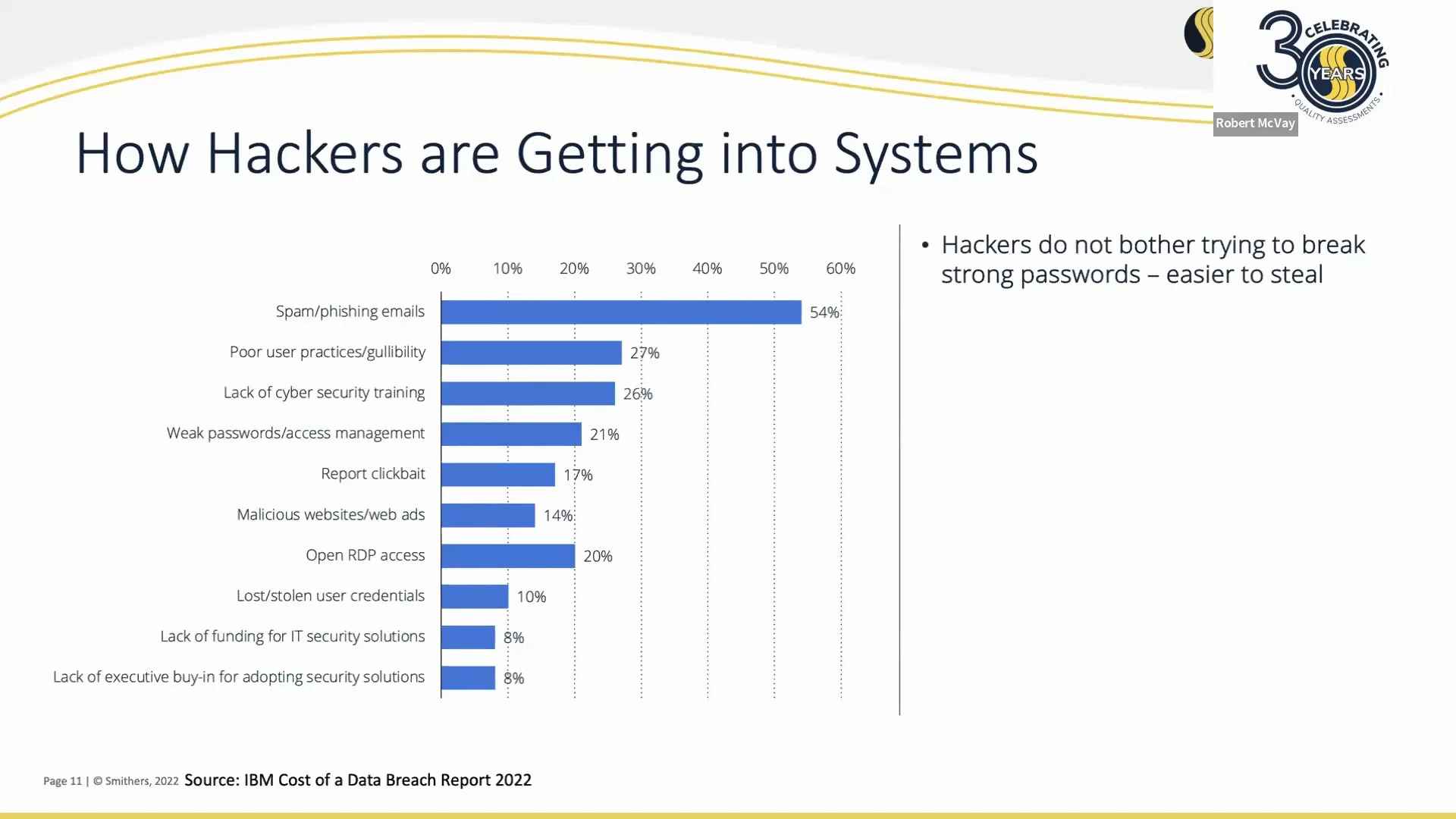
The Cost of a Cyber Breach
September 13, 2023
Talk about cybersecurity breaches is increasing, but the potential cost of a cybersecurity incident is harder to pinpoint. Much depends on the size of the organization, but that is not the only factor. As Robert McVay notes, small to medium-sized businesses are currently being attacked at increasing levels. The cost of a cyber breach is not just the lost data. It is lost productivity, legal costs (potentially), and more. Learn how much a cyber attack might cost you and why you should work hard to protect your organization.
Enter your email address to view this video.
54:20
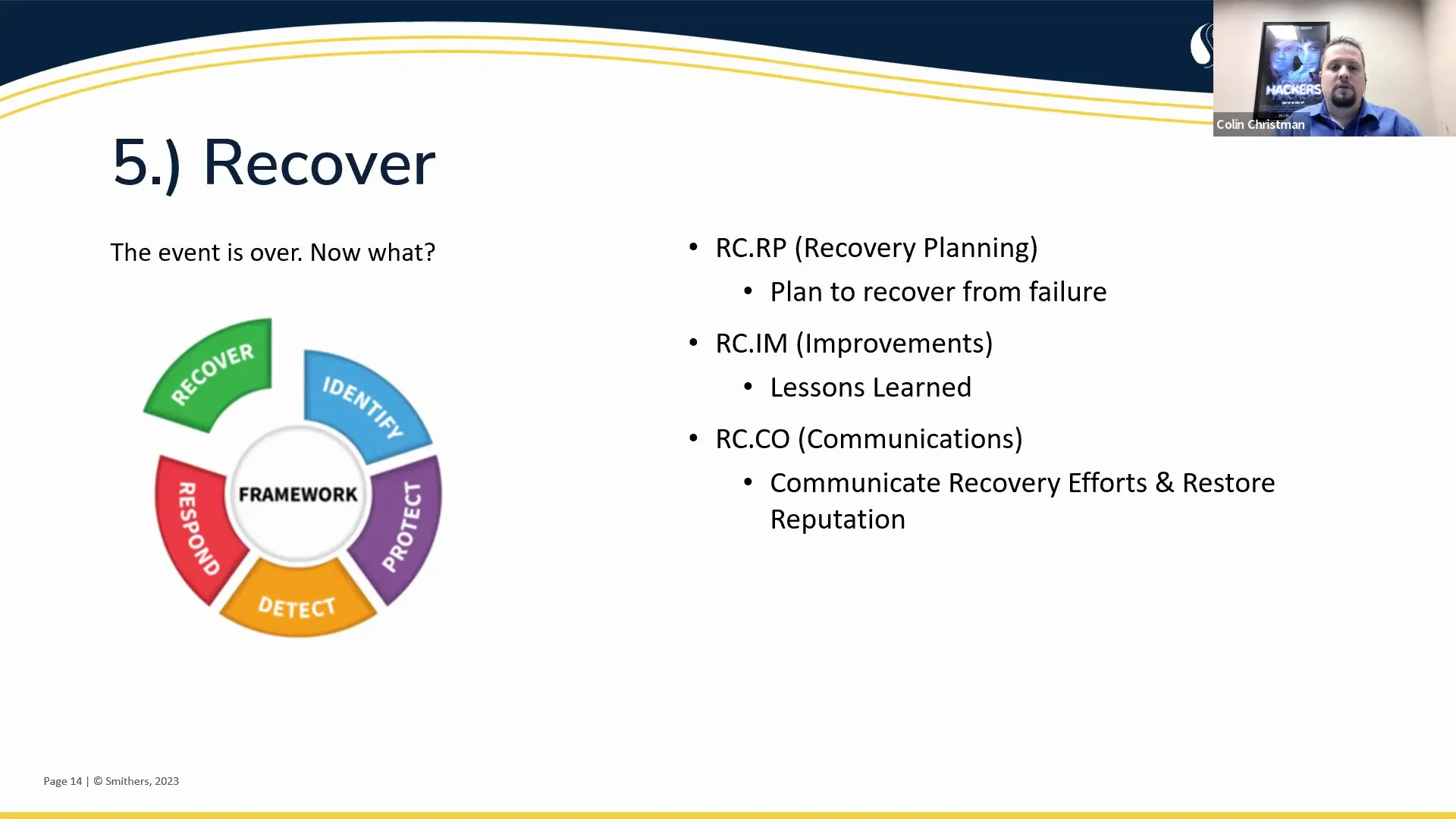
NIST CSF For You
August 2, 2023
Currently, NIST SP 800-171 is on everyone’s radar because of its close ties to CMMC 2.0. The NIST Cybersecurity Framework is different. As Smithers Senior IT Manager Colin Christman notes, the NIST CSF will help you protect your organization’s data by offering an organizational structure for risk assessment and prevention. However, the CSF is not a standard to which an organization needs to be certified. Watch this webinar to learn more about the NIST CSF.
Enter your email address to view this video.
40:10
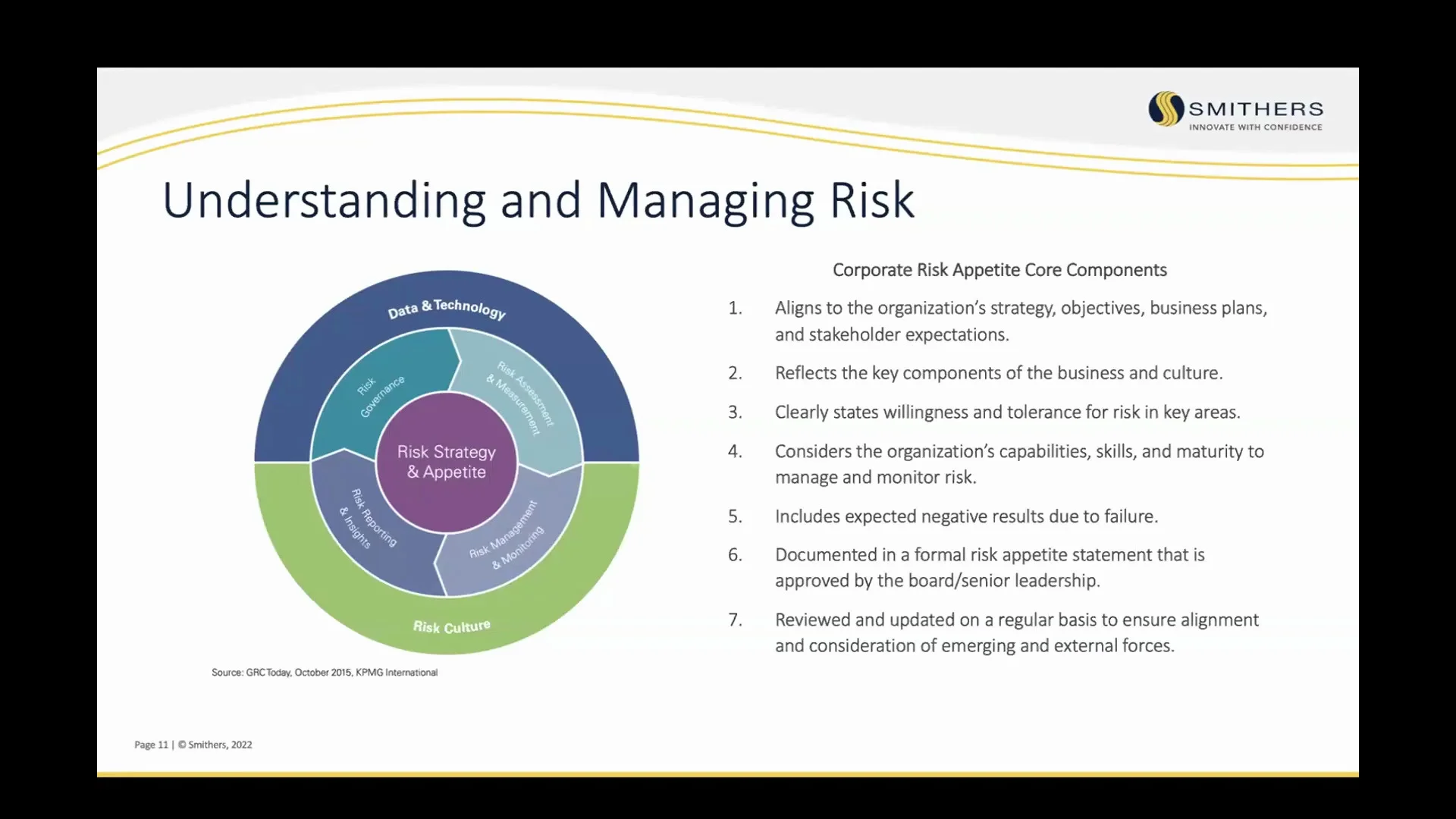
How to Understand and Manage Cybersecurity Risks
July 25, 2023
Who has to worry about a cybersecurity attack? If you think you are safe because your organization is small, you are actually the perfect target for a hacker. In this webinar, Robert McVay defines the different kinds of cybersecurity risks, what kinds of businesses are being targeted, and what steps can be taken to help prevent a serious breach.
Enter your email address to view this video.
1:01:04